A question was asked on Quora about suspicious behavior of 'Coffee Meets Bagel' Android app. I thought to perform some analysis on this app. I didn't have much time to thoroughly look into this app, so following are preliminary results of the analysis.
The app asks for following set of permissions:
Permissions:
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.RECORD_AUDIO"/>
<uses-permission android:name="android.permission.CAMERA"/>
<uses-permission android:name="android.permission.GET_ACCOUNTS"/>
<permission android:name="com.zigct068.ddixg911.permission.C2D_MESSAGE" android:protectionLevel="signature"/>
<uses-permission android:name="com.zigct068.ddixg911.permission.C2D_MESSAGE"/>
<uses-permission android:name="com.google.android.c2dm.permission.RECEIVE"/>
And for a broadcastreceiver, it has following permissions
<receiver android:name="com.qbiki.gcm.GCMBroadcastReceiver" android:permission="com.google.android.c2dm.permission.SEND">
<intent-filter>
<action android:name="com.google.android.c2dm.intent.RECEIVE"/>
<category android:name="com.zigct068.ddixg911"/>
</intent-filter>
</receiver>
Permissions and App Behavior:
<uses-permission android:name="android.permission.INTERNET"/>
The app needs this permission to download ads data and opening youtube videos etc. It may use it for other purposes, of course.
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"/>
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
Almost all the ad libraries including Google libraries use geo-location coordinates to obtain customized advertisements. Though some apps may encrypt this data before sending it out but most of them don't. If you are concerned about your location tracking, probably you should always use paid apps with no ads. Well, you still can't escape Google.
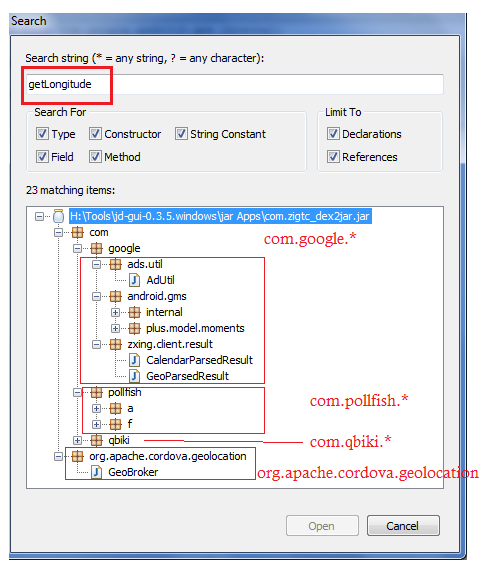
Here is quick search of getLongitude api call which returns longitude coordinate of the device (user). You can assume that at least these packages use location coordinates.
Following are four main packages:
1) com.google.* - Google ad libraries and other libraries use location information
2) com.pollfish.* - It's another library that allows developers to survey their users. These surveys are based on geo-location coordinates, device resolution, screen size etc.
3) com.qbiki.* - This package contains original functionality of the app. I discuss it later.
4) org.apache.cordova.* - discussion is given below.
First two packages are from reputable organizations, so we can pretend to know that they won't abuse our private data.
4) org.apache.cordova.*
Apache provides a development framework using which you can build android as well iphone apps without actually writing code for it. You write code using apache API and it will create android and iphone apps for you. Cool. Isn't it?
To use apache framework, you need to mention a list of libraries you want to add into your application i.e. one library for each different functionality. And each library needs required android permissions, obviously. For example, in case of camera functionality, you need to specify following items:
Anyway, for the running app (Coffee meets bagel), the app developer has specific all the libraries apache provides, in its config.xml file (/res/xml/config.xml)
So to avoid breaking the app, the developer needed all those permissions. It is still unsure if the developer actually used any functionality or not.
Decompiling and Recompiling the app:
By looking into the dalvik byte code of the app, it appears that the developer has just added these libraries and probably is not using their functionality. So I decompiled the app, removed these libraries, removed following permissions,
<uses-permission android:name="android.permission.RECORD_AUDIO"/>
<uses-permission android:name="android.permission.CAMERA"/>
<uses-permission android:name="android.permission.GET_ACCOUNTS"/>
recompiled the app and installed the app on my device again. So far, it is working the same as it was doing with the original version.
** Ideally, if the application invokes any API for which it does not have any required permissions, the app should crash but it is not doing so far. So, most probably, the app is not using much from org.apache.cordova.* library.
Suspicious code (com.qbiki.*):
The cordova libraries have code that can record audio/video files on the device. Similarly, in its original package code, com.qbiki.*, it contains code that can upload image files to the server. To be specific, com.qbiki.feedback.FeedbackFragment.submitfeedback() contains that code which can potentially upload image files to the developer's chosen server. But is this code actually executed or not?
Network traffic analysis:
I've played with the app for one day, executed roughly all of its functionality, monitored its network traffic for a few hours via tcpdump, and analyzed the traffic via wireshark. I took traffic dump at two different intervals and analyzed them. The app leaks some information about the device but I think, that's what every applications does now a days.
However, it does not seem to uploading images to the server. It does download a few files from the server such as
XML: http://seattleclouds.com/myapplications/_publishers/appxygen/babydekdee/2162014coffeemeetsbagel/app.xml
Java script file: http://s.ytimg.com/yts/jsbin/mobile-blazer-nirvana-phone_mobile_blazer_noncore_nirvana_phone_mod-vflthpDZb.js
Performs registration of the app with the sever.
http://push.seattleclouds.com/gcm_register.ashx
It did not consume the link given in submitfeedback() method so far. But it is quite possible, it can.
App Specific Files
The app contains functionality that can record audio files and store it in its app specific folder (/data/data/com.zig ... ). I have kept this app running for one day, obtained files from the location and analyzed them, but have not found any recorded audio or video files there. However, the app has permissions and code to store files on external memory (sdcard/Android/obb/) but I couldn't find anything suspicious there.
Conclusion
First of all, the app is a fake app. It does not do what it is supposed to do. It is not from the official CMB organization. However, its counterpart app on Apple app store is original.
Secondly, it has all required permissions (Camera, Contacts etc.) and potentially malicious code to exhibit malicious behavior (recording audio/video files and uploading it to the server). Probably I have missed those triggers or that code is executed after receiving some commands from the server.
If I have time in the future, I will spend some more time on it.